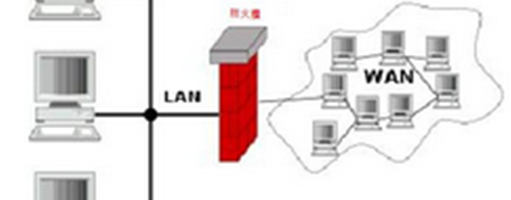
Diagnosis of information security and information update
We will make a preliminary assessment for the security of your information. This service mainly includes inspection of your facilities and information flow by a comprehensive method. We will provide you a report, pointing out the possible weaknesses of the systems and information processes and detailed steps to settle these weaknesses. If you have technical difficulties, we will also assist you to overcome them.
For our report will be sorted according to the severity of the weakness, the more serious weaknesses are recommended to repair with high priority. These parts involve wide ranges including the company’s software, hardware, and operating procedures. For example, the design of the network structure makes the internal computer to get better protection for safety communication to prevent leakage of secret information, and the correct set of routers, firewalls, proxy servers, and so on.
In addition, as the information technology becomes increasingly complex, the hacker tactics are ever-changing. We will get the latest information at the first time and assist you in patching security vulnerabilities for protecting against the latest attack.
Information security training
Information security problem can not be completely solved only by hardware and software alone. Since internal staff do not have the correct knowledge of information security, or comply with the security rules, the company’s information security may be exposed to risk. For example, the common social engineering attacks are specially made for employees without the knowledge of the information security.
Ray Aegis provides information security training courses, so that customers will not take the risks of information leakage due to human error.
Safety and risk management, policy development
With the latest technological developments, we help the company assess the risk, lower the probability of occurrence of problems, and also assist companies to make real-time monitoring, as well as the development of security policies. In cooperation with the professional law firm, we assess these policies and help the company to correctly implement the policy.
IT management and regular analysis reports
Management technology infrastructure requires knowledge and skills, and is full of challenging. Usually a company makes use of the concept of cost-effective to integrate different technologies to accomplish task. Clear division of responsibilities, effective enhancement of the interaction between the different facilities and people, confirmation about problems to be solved and timely monitoring are first steps to manage your IT facilities to meet the company’s needs.
Then, let all facilities that work together to achieve the company’s goal and to solve any unexpected situation at any time. We help companies establish or improve current IT facilities and assist in the improvement of operations and information flow, so that everything runs efficiently based on security. In addition, we regularly analyze the security of the system, with or without signs of invasion, and keep your facilities in the safest state with the up-to-date information.
Uninterrupt service planning
Many disasters can not be avoided (such as typhoons, blackouts, fires, etc. ), and well advanced prevention is very important. Our company is planning the security system to build depending on your cost, so that your system can function normally even in the face of force majeure.
Evidence
If your system is attacked or detected leakage of confidential documents, Ray Aegis can help you identify the root cause by analyzing evidence from the computer system and help improve. This work can identify the source of the attack to obtain relevant evidence and the company’s legal rights will be reserved. In addition, if the hack attack is not successful, we can also identify the people trying to attack, analyze the hacking methods by accurate software analysis, and then strengthen security prevention accordingly.
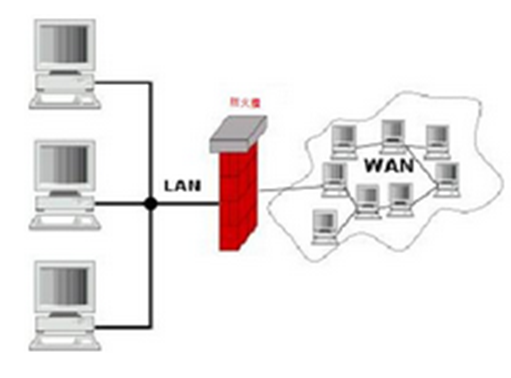
Network Monitoring
We analyze instant status of the network and detect suspicious behavior, such as hacking attack on your system or Trojans in computers.
You worry about hackers always want to intrusion system, causing many problems? Our real-time monitoring blocks off all unnecessary risks!
You worry about staffs leak internal confidential documents by email or other means of communication? Technology monitoring, as well as security policy make all these distress not occur!