SandSphere is an advanced tool for analyzing potential threats and backdoors in programs. Utilizing patented dynamic and static analysis techniques, it identifies whether codes, executables, libraries, and third-party components are misused by various malicious programs and backdoors.
Customers can use SandSphere to check whether the programs or third-party components delivered by outsourced vendors contain malicious programs or backdoors.
Currently, many large financial control companies, government agencies, and enterprises, both domestically and internationally, use SandSphere for security inspections before systems go live, successfully preventing numerous major security incidents.
Features of SandSphere:
- Detects all hidden connections, backdoors, and malicious programs within the code (inspects whether the system or program contains malicious programs and backdoors).
- Meets security control requirements, ensuring the security of third-party components and outsourced development systems.
- Scan reports clearly list the file paths at risk and the reasons for the alerts.
- Analyzes the reputation of global websites and regularly updates the C&C server list (detects malicious website links and regularly updates the malicious website list).
- Supports various file types and searches for known and unknown threats within the code.
- Customers can choose to use either self-built hardware (appliance) or cloud services to automate regular code security analysis.
Samples of SandSphere Detection:
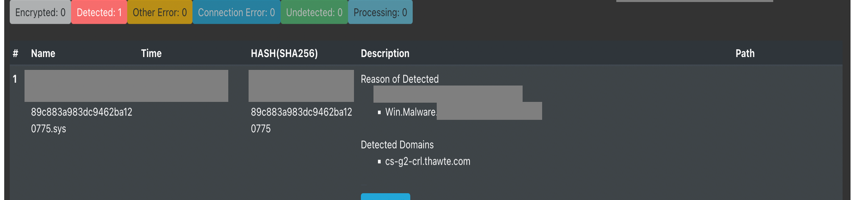
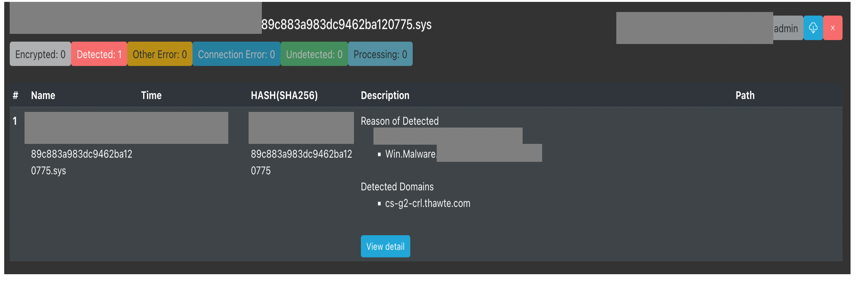
A .sys file has been detected as a Windows malicious program. It steals sensitive information and uploads it to a C&C server. This example shows how SandSphere uses domain reputation ranking to identify malicious domains within a program, which other antivirus software cannot detect.
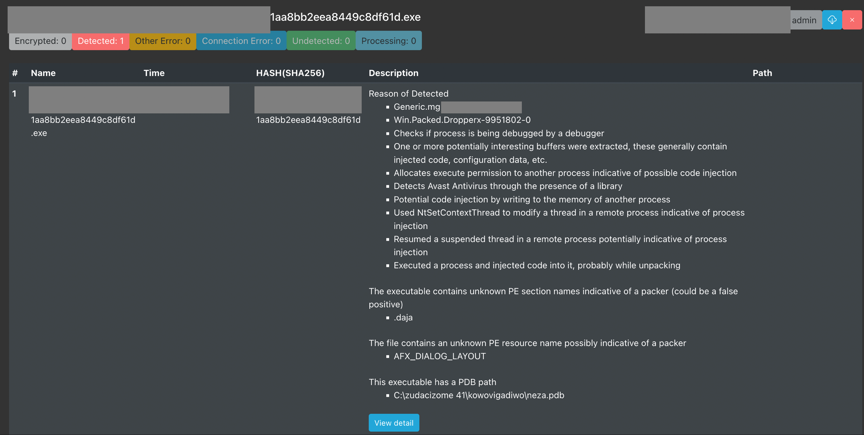
An .exe file has been detected as a malicious program. It detects whether antivirus software is running, injects code into other programs, and is protected by packing. Because this hidden virus is protected by packing and it detects the presence of antivirus software in the system to alter its behavior, no other anti-hacking programs or sandboxes can currently detect it.